Approach
Our threat detection methodology aligns with the cyber kill chain framework and strictly follows the industry standards like ISO 27001, ISO 27701, NIST, PCI-DSS, and SOC 2 Type II.
Features

Approach
Our threat detection methodology aligns with the cyber kill chain framework and strictly follows the industry standards like ISO 27001, ISO 27701, NIST, PCI-DSS, and SOC 2 Type II.

Accelerators
Our library of 100+ resulable accelerators enables quality and on time delivery of projects like :

Agility
We provide 360˚ cybersecurity service offerings tailor-made to meet customers' requirements. We adopt an AI security approach to achieve a proactive state of cyber maturity & resiliency.
Service Offerings
Vendor Risk Assessment Services
Our risk management platform helps you pinpoint, measure, and prioritize your third-party cyber risks, so you can plan appropriately and sleep soundly.

Vendor Risk Assessment Services
Zero Trust Architecture Services
Give the Right People Access to the Right Resources. At the Right Time.
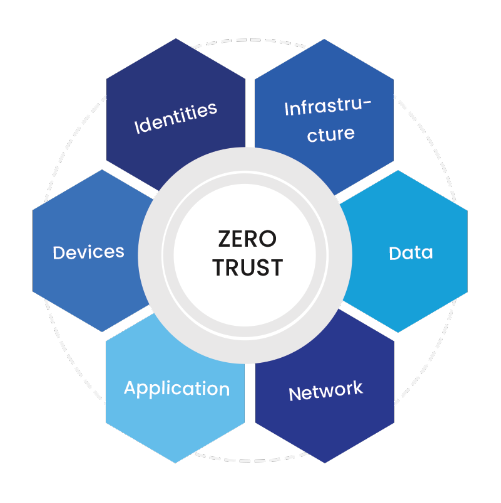
Zero Trust Architecture Services
Featured Case study
Their primary vendor risk assessment pain points were:
Finance
Industry
Information Tech
Solution
Data Piper
As a major consulting firm, lines of services distributed globally leverages multiple methods and tools to acquire data from clients and share the analysis / insights. Firm needed a modern way to :
Their primary vendor risk assessment pain points were:
Finance
Industry
Information Tech
Solution
Data Piper
Solution
Assessed their vendors for the following:
Result
Estimated time spent on vendor sourcing and selection:
Estimated time spent on vendor intake and onboarding: